Among the various smartphone manufacturers, Mediatek is a prominent player, producing many devices with different chipsets and features for diverse user bases. However, just like any other smartphone, Mediatek chipset smartphones are also prone to brick on multiple occasions. Previously, it was easy to flash any bricked Mdiatek (MTK) smartphone and bring it to life again. However, due to modern security practices, many smartphone manufacturers have put special authentication on their devices, making it impossible to Unbrick Any Mediatek Phone Without Auth File.
A bricked MediaTek smartphone refers to a device that is not booting up, is stuck in a boot loop, and downright not functioning properly, making it useless as a brick. This situation can arise for various reasons, including failed software updates, custom ROM installations, attempts to root or unlock the bootloader, and flashing custom-made scripts for Android developments. While encountering a bricked Mediatek phone can be a daunting experience, there’s a glimmer of hope for users who find themselves in this situation, as XDA Developers experts say that an MTK device can always be brought back to life.
However, many smartphone manufacturers, including Oppo, Realme, Oneplus, Xiaomi, and others, are opposed to this idea of hardbricking and flashing of smartphones with custom ROM and other scripts. Due to this, these companies have set up special authentication rules that make it difficult to access these devices when they are in brick mode or download mode. If you are also facing such situations and wish to Unbrick Any Mediatek Phone Without Auth File then you need to read this article.

Page Contents
What is Mediatek Phone Auth File
Devices with MTK chipsets have different download modes, including the BROM (Boot Read Only Memory) mode, which typically loads the preloader file, which helps the device boot the Android operating system. The BROM mode also starts the OEM download mode, which is strictly intended for OEM servicing and can be used to flash stock firmware or firmware upgrades.
However, access to this mode is restricted to OEM service center professionals only since device manufacturers have started obfuscating the process. Including a special authentication or auth file a specially signed download agent by the corresponding OEM manufacturer. This means that you can’t flash or unbrick your smartphone unless you have permission from the device manufacturer.
Can You Unbrick Any Mediatek Phone Without Auth File
Mediatek Smartphones come with Emergency Download Mode so essentially these devices can always be unbricked if you have the right tools and the right firmware with you. However many smartphone manufacturers have put special measures to revoke this access by using auth files. These auth files can only be used by OEM service representatives to get access to the hardware memory of your smartphone. However several developers from the XDA developers community have discovered some exploits that you can use to bypass the auth file requirement.
There are currently several exploits available in the market, but most of them are built on boot ROM exploit discovered by XDA senior members namely xyz`, developers Dinolek, and k4y0z. This involves a generic bypass mechanism that can bypass the authentication while flashing of custom firmware or stock ROM. In simpler terms, this technique uses special bypass address codes designed for MediaTek smartphone chips. These auth bypass codes help override the authentication asked by a flashing tool called SP Flash Tool before flashing the phone firmware.
How to Unbrick Any Mediatek Phone Without Auth File
In the below guide, we will be taking advantage of all the possible methods by which you can Unbrick Any Mediatek Phone Without Auth File. This involves the process of using several known exploits to bypass “Serial Link Authentication (SLA)” and “Download Agent Authentication (DAA)” flags.
After bypassing these auth file flags, you will be able to access the download mode memory and can flash your device using SP flash tool or MTK flash tool. So without further ado, let’s get started with the guide below to Unbrick Any Mediatek Phone Without Auth File.
Warning
Prerequisites & Downloads
Before we move toward the different methods to Unbrick Any Mediatek Phone Without Auth File, we must understand how to flash the phone using SP flash tools or MTK flashing tools. It’s also important that we install all the required drivers and libraries to make this process work. Below is a list of downloads and requirements that you must fulfill before following the guide.
Downloads
Download & Install Python 3.7.3 – Click here
Load pyusb pyserial json5 Library – By command “pip install pyusb pyserial json5”
Download & Install CDC_ACM Drivers – Click Here
Download & extract SP Flash Tool v5.23 – Click Here
Download MTK USB PORT Hardware Driver – Click Here
Download & Install libusb – Click Here
Download & Install USBdk (If libusb doesn’t work on your system) – Click Here
Once you have downloaded all the required drivers and filed from above, please complete all the pre-requisites to comply with the process below.
Prerequisites
- Make sure you have the correct region firmware for your advice (If you install JP version ROM on an EU version device, it will brick it and lock the bootloader)
- Make sure to install Python and enable environment variables in the python setup.
- Load pyusb pyserial json5 library in python and keep Python running in the background.
- Run libusb tool and install the device filter for your MTK bricked device.
- Make sure you have the correct Download Agnt & Scatter File for your corrosponding device firmware.
Method 1: By Not Flashing Auth Images
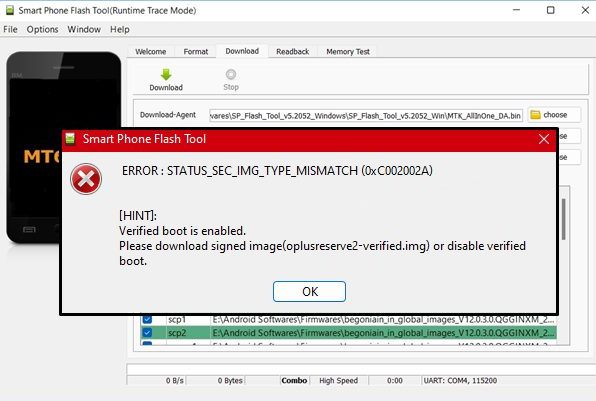
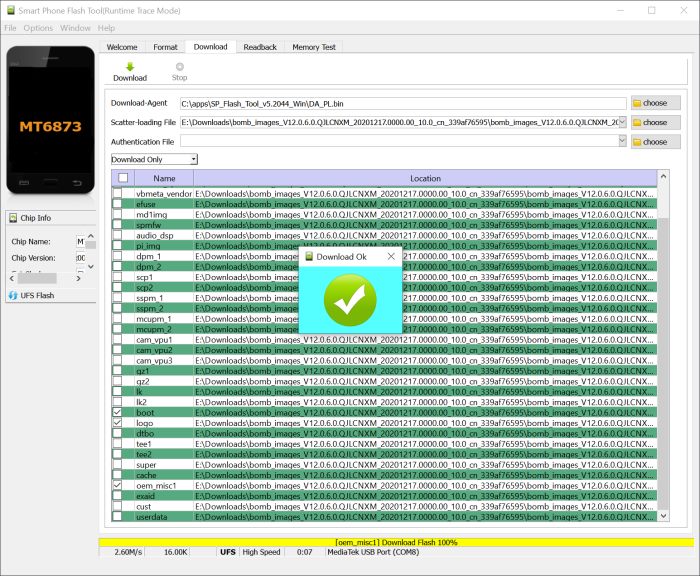
When you try to flash the boot image files on your bricked Mediatek device, you will be given a warning – “SEC IMG TYPE MISMATCH” claiming you to download some verified image for the firmware. In most firmware, only 2 files named – “oplusreserve2.img” & “cdt_engineering.img” can throw this error. For this, you can simply exclude these files from the flashing process.
Method 2: Using MTK Bypass Utility
MTK Bypass Utility is a Python command line tool developed by chaosmaster & Dinolek. This tool can easily bypass the SLA authentication on various Mediatek devices. You may proceed with the below steps to bypass MediaTek SP Flash Tool SLA and DAA Authentication for supported Mediatek SoCs.
- Go to the MTK Bypss tools folder press the Shift key + Right-click on the mouse to open up the context menu.
- Here select Open PowerShell Window here from the list.
- Then copy and paste the following command line and hit Enter to run the main.py python file:
python main.py
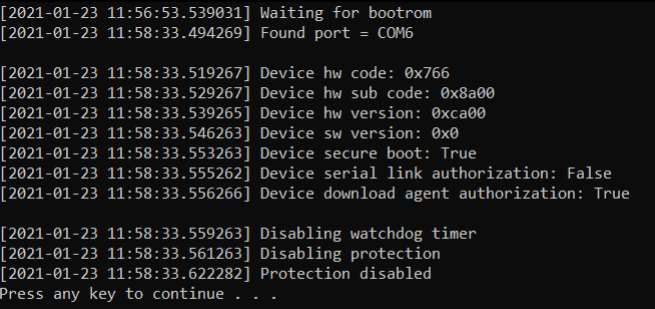
- Once done, you should receive a notice or popup “Protection Disabled, Press any key to continue”.
- Just press any key to continue and then open the SP Flash Tool to continue with the flashing process.
Method 3: Using MTK Auth Bypass Tool
MTK Auth Bypass Tool commonly known as MABT Boot in the Android community is a powerful tool with an advance set of instructions ranging from preloader dumping, OPF extracting and disabling Auth for Mediatek smartphones. You may proceed with the below steps to bypass Auth file for supported Mediatek SoCs.
- Open the MTK Auth Bypass Tool and click on Disable Auth button.
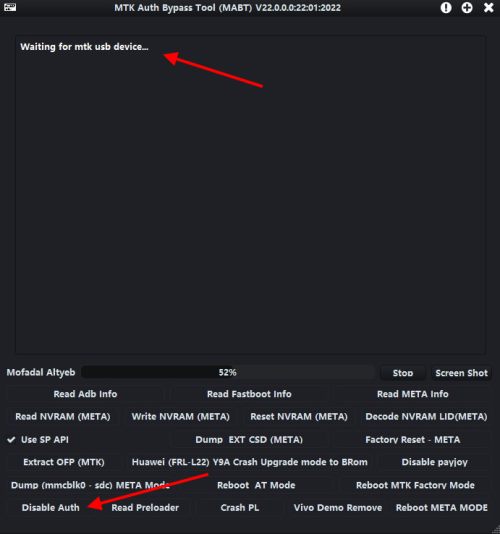
- Connect your MTK device in BROM mode by pressing all hardware buttons (Volume Up + Volume down + Power key) and wait for the tool to connect the device.
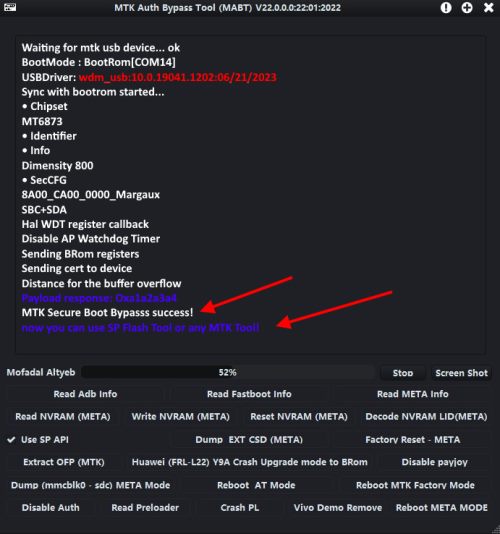
- Once the device is connected, the MABT will bypass the authentication, upon which you can flash your device with SP Flash Tool.
Method 4: Using MTK Client
MTK Client is also a reliable tool made by a developer known by name bkerler. The tool has the capability to bypass Auth and installation of apps and various scripts and kernel image files. You may proceed with the below steps to bypass Auth file for supported Mediatek SoCs.
- Download and Extract the MTK Client Folder.
- Press the Shift key + Right-click on the mouse to open up the context menu.
- Here select Open PowerShell Window here from the list.
- Then copy and paste the following command line and hit Enter.
pip3 install -r requirements.txt python setup.py build python setup.py install python mtk payload
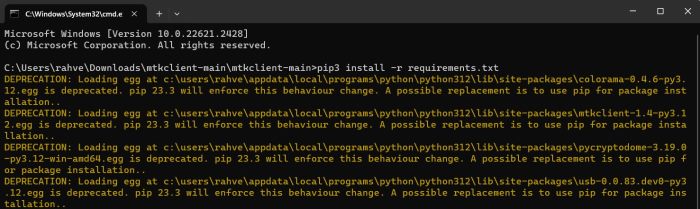
- Now connect your MTK device in BROM mode by pressing all hardware buttons (Volume Up + Volume down + Power key) and wait for the tool to connect the device.
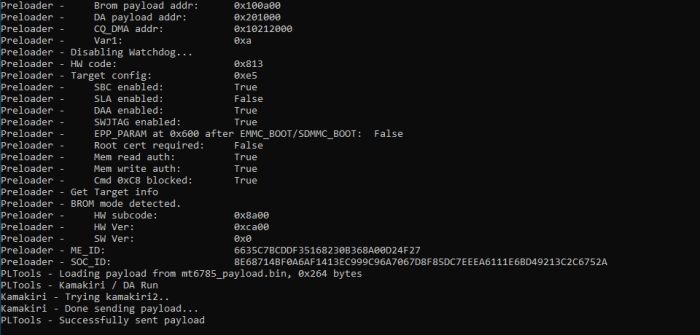
- Once the device is connected, the MTK Client will bypass the authentication, upon which you can flash your device with SP Flash Tool.
Method 4: By Dissecting BootROM
If none of the above methods helps you, then most probably the Mdiatek device you are using is quite new with the latest MTK chipset which doesn’t work on previous exploits. For such a case, you have to generate your own exploit by using the method below.
Warning
Here is a step by step simplified process to create your own MTK exploit by Dissecting BootROM. If you have any confusion regarding the process, then you may refer to the original guide for dissecting BootROM exploit here.
Dissecting a MediaTek BootROM exploit
byu/yohanes inReverseEngineering
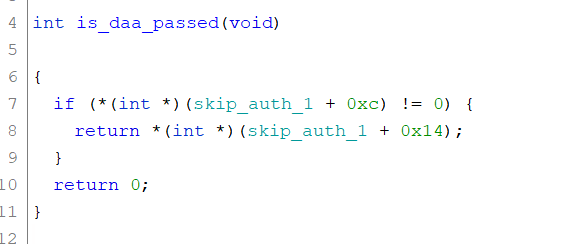
BROM can have SLA (Serial Link Authorization), DAA (Download Agent Authorization), or both. SLA prevents loading DA if we are not authorized. And DA can present another type of authentication. Using custom DA, we can bypass the DA security, assuming we can bypass SLA to allow loading the DA.
- First Dump BootROM of your device using any command line MTK tool.
- Open the dumped file using binary ninja
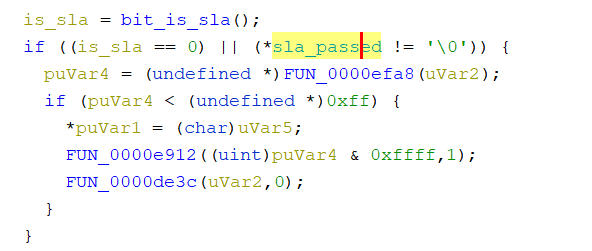
- Edit the function name – bit_is_sla() & is_daa_passed() to bypass auth.
- Once done, save the file and flash the modified DA file on your phone.
- Now you can boot into download mode and flash custom firmware using SP flash Tool.
Conclusion
This brings us to the end of this guide for How to Unbrick Any Mediatek Phone Without Auth File. I hope the above guide has helped you to bypass the Mediatek authentication and now you can easily flash the stock ROM or custom firmware that was obstructed by the missing auth file. However, please note that flashing your device with custom ROM and scripts will definitely void your device warranty. In case you are looking for your device firmware, then please move to our Android Tips & Tricks section to find all the latest news about stock and custom ROMs and rooting processes.