Amazon Web Services (AWS) is considered the world’s most comprehensive and broadly-adopted cloud platform. They provide a wide and reliable range of tech infrastructure, scalable cloud computing services that are on-demand to millions of consumers on a metered pay-as-you-go basis. Of course, with this level of sophistication might come some security concerns consumers might have. In this article, I’ll be talking about what Amazon Web Services Security Groups are and how they can be used to protect your EC2 instances on AWS.
Also Read

What is an AWS Security Group?
An Amazon Web Service security group is simply a virtual firewall for your instance to control (filter) incoming and outgoing traffic.
How To Create AWS Security Groups
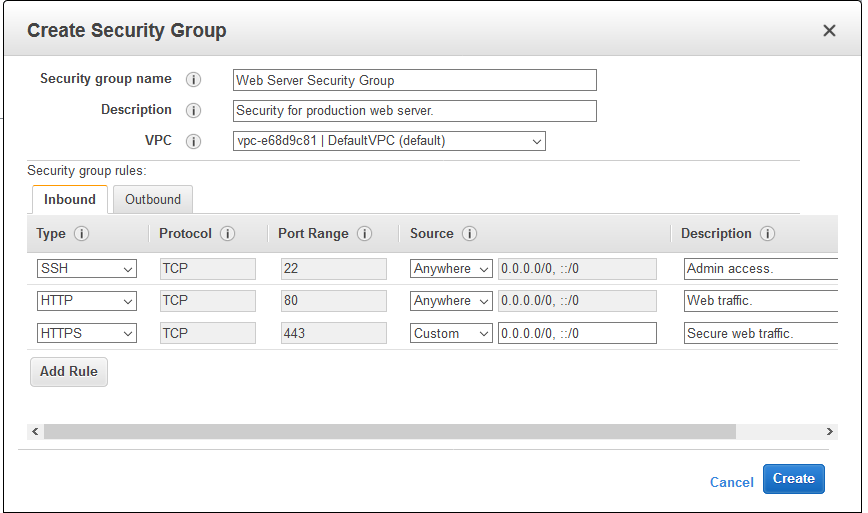
There are multiple ways to create an Amazon Web Service Security Group, one of which is through the AWS management console, another method is via the Amazon Web Service Command Line Interface(CLI).
In this article, I’ll be showing you how to create a security group from the AWS management console.
- Login to your AWS Management Console.
- Select the EC2 service.
- Select “Security Groups”, it can be found under the “Network And Security” category.
- Click on the “Create Security Group” button.
- Input your security group name and description.
- Select your corresponding VPC.
- Add and configure your rules.
How to Configure & Optimize your AWS Security Groups
Here are a few tips on configuring new Security Groups in AWS, and optimizing existing ones.
Remove Unused groups
You might have created a security group for running a test while trying to figure out how security groups work. It is advised that you remove/delete any unused security group.
Enable Alerting and Tracking
Amazon Web Services comes with a nifty tool called AWS Cloudtrail that enables its users to keep track, continuously monitor and retain account activity related to actions carried out in your AWS infrastructure.
Avoid Inbound traffic via 0.0.0.0/0
As stated early, using the anywhere 0.0.0.0/0 value has to be on a need to basis and a complete understanding of what you are doing.
However, it is recommended that you keep away from this completely because it could end up exposing sensitive data to the outside world.
It’s best practice to only give access to specific Protocol and port ranges; this ensures that other incoming packets will be dropped.
Roles of Amazon Web Services Security Groups
Like I mentioned earlier, security groups are basically virtual firewalls and act as such. Providing security to your Amazon Web Service EC2 instance by filtering inbound and outbound traffic at both protocol and port levels.
Every Security Group (read: firewall) is slightly different from Network Access Control Lists (NACLs) as they do not possess a “Deny” rule. What this means is, packets will be dropped if there were no specific rules assigned to them.
When creating a Security Group, your primary objective is to restrict access so you can also help maintain what traffic goes in and out. You should also strive to give each group a very distinctive name and description so as to reduce the chances of errors.
Security Group Rules
Rules in your Amazon Web Service Security Groups are simply a way of filtering what inbound and outbound traffic are allowed. You can also consider them a way of authorizing or revoking incoming and outgoing access.
You can grant access to specific Security Groups, IPv4 or IPv4 addresses or specific CIDR(Classless inter-domain routing) range.
Here are a few basic Security Group Rules:
- Automatic Destination: Whenever you add a security group rule using the Amazon Web Service Command Line Interface (CLI), AWS automatically sets the destination CIDR block to a canonical form.
- Strictly Inbound Rules: This applies to any source of traffic moving into your Virtual Private Cloud VPC. These sources can be another Security Group or a single IPv4 or IPv6 address.
- Outbound Rules: Outbound rules deal with the destination for incoming traffic. They can be routed to a different Security Group, a CIDR block or a single IPv4 or IPv6 address.
Inbound and outbound security Group Rules comprises five different fields: Source, Protocol, Port Range & Description.
Source
This is usually a custom IP address, a subnet range or another security group. You can also grant access to the entire internet if you use the “anywhere (0.0.0.0/0)” value.
Using the anywhere (0.0.0.0/0) value has to be on an as-needed basis, and you should completely understand what you are getting into.
Protocol
Protocols typically default to TCP and tend to be greyed out. If you are working with custom rules you created, however, you can modify the protocols to fit your needs.
Port Range
Port ranges are typically pre-filled. However, you can decide to work with a custom port range of your choice.
Descriptions
This is the field where you insert a description for the rule you have created. It can be helpful to make it detailed.
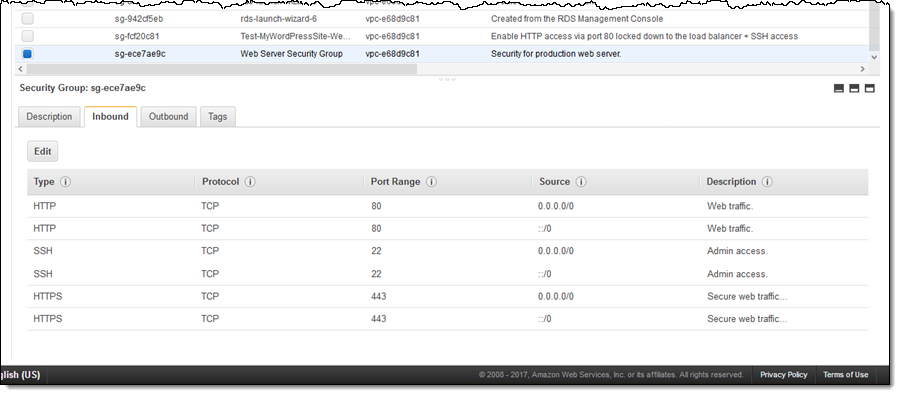
Amazon Web Service Security Groups puts a lot of power in your hands, all the while ensuring things stay safe and secure.