Most of the time, the Internet can be a scary place to roam. Needless to say, we are under frequent attacks from malware and Ransomware whenever surfing the web. But to protect ourselves we have antivirus and internet security software, that do their job pretty well. But not all the time, they are as reliable, as the attackers are continuously searching for loopholes in the security system of the users. So here comes the most popular title, VPN, aka Virtual Private Network. VPNs commend to safeguard users from online tracking and other security threats that can always be helpful.
Now the users here are hearing a new name in this field, that is, Proxies. We would like to tell you. Proxies are not new. Actually, they were available even before the release of the first Virtual Private Network Server on earth. Proxies do the same thing as the VPNs, and just the approach is slightly different. Today we are going to do a comparison guide to help the users understand which is better for them and why. So let’s get started.
Also Read
Free Proxy Address for Telegram | List of All Proxy Server 2023
Free Proxy Address for WhatsApp | List of All Proxy Servers 2023
Fix: Certificate Validation Failure on VPNs
All Unblocked The Pirate Bay Proxy List 2023
List of All RARBG Proxy List (Working 2023 Update)
How to Fix IPTV Not Working with a VPN
Fix: NordVPN Not Connecting on iPhone, iPad or Mac
Page Contents
What is a Proxy Server?
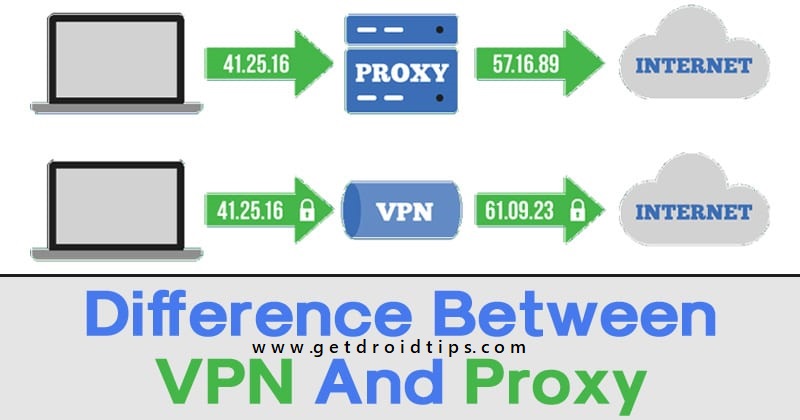
A proxy server acts as a connection terminal between the websites you are visiting and your current device. The device is connected through a third person or a middle man that is a remote machine that is again connected to a host server. This middle man is your Proxy. The proxy server then connects to the website, it hides your original IP address (Internet Protocol) and uses some other IP address. This is the worst thing about Proxies, and it usually follows the algorithm of using the IP addresses of other users on that network. Let us make this clear with an example, suppose you are in India and using a specific Proxy, and then again, a user in Africa is using the same proxy. Now proxy servers will interchange their IPs in order to make the websites think that the user in India is in Africa and vice versa.
Proxies don’t make out with original or entirely different IP addresses that form a kind of loopholes in the eyes of an attacker. However, we would like to add that Proxies only work on the application level rather than tunneling the whole device. It means that if you are using a Proxy for a particular application, only that application traffic will be rerouted.
There are mainly three types of Proxy Servers:
HTTP Proxies
HTTP stands for Hyper Text Transmission Protocol, and you usually notice them at the front of any webpage you’re trying to access. It is automatically added before that. So, from this, you can understand that HTTP Proxies work only for web pages. So all your browser traffic will be rerouted through this proxy. Hence it provides a semi-secure environment for browsing. Let’s move on to the other proxies.
SOCKS Proxies
SOCKS is an internet protocol that routes the packet data between the server and a client using a Proxy server. Then a temporary IP address is generated for further processing. It is a good proxy still it works on application-level like on a game or anything that involves a person to person protocols. They are, however, very slow since they are under high load. This is because they are the most used Proxies in the world. But as they work on P2P protocol, this makes them slower than HTTP Proxies. Now, let’s move on to the last Proxy.
Transparent Proxies
These are ordinary Proxies with their primary job of censorship and monitoring. They are really very slow and work when they get your real IP address. On getting confirmation from the Proxy Server, they reroute the traffic through your browser or application whatever it is. Usually, colleges and offices use this type of proxies to authenticate their users and keep a close eye on what they are doing. Home users may also use it to monitor their kid’s talents on the internet ?. The only good thing about this Proxy is that the users can set a usage bandwidth.
Pros of Using Proxies
We will now look at the positives of using a Proxy.
- You are safe from online attackers to some extent
- Google will not disturb you with irrelevant ads
- You can use Proxy as a monitoring tool
- Most of the Proxies are free to use
- They do not slow down your internet
Cons of Using Proxies
We will now look at the negative side of using a Proxy
- They work on application level hence decreasing the overall security
- Proxies usually interchange the IPs of users with others that make them vulnerable to attacks
- Good Proxies come at a reasonable cost
- When using Proxies as an authentication tool, they leave the network unmasked hence compromising the overall server
What is a Virtual Private Network?
We can say that a VPN works in the same manner, just like a Proxy. The main difference here is that VPNs work with tunneling the whole device to bring a more secure environment to the users. Tunneling the entire device means it works on the operating system level provides a layer of security over browsers as well as applications. VPNs don’t interchange IP addresses for other users, and instead of that, it provides an entirely different IP address whenever the user turns on the VPN.
A VPN also encrypts the traffic that is sent through it, which means what happens between your device and the server. Stays with the server, and thus you are at no risk of data breaching and attacks. Further, the VPN also protects you from location tracking and government surveillance. So that you can access websites that are not available or banned in your country. You know better about those websites, and thus we recommend you use a VPN to get ultimate online security and privacy.
Pros of Using a VPN
Now we will look at the positives of using a VPN
- VPNs are most secure because they tunnel the whole device
- VPNs use subnet masking so that the attacks cannot target your IP address
- They use different IP addresses every time you connect with varying attributes of the location
- VPNs can be used to access websites that don’t allow access in a specific region
Cons of Using a VPN
We will now look at the negatives of using a VPN
- Generally, VPNs are quite slow to operate
- Fast VPN services are costly and more difficult to maintain
- They frequently get disconnected
- Unpaid VPNs sometimes share sensitive information with other websites
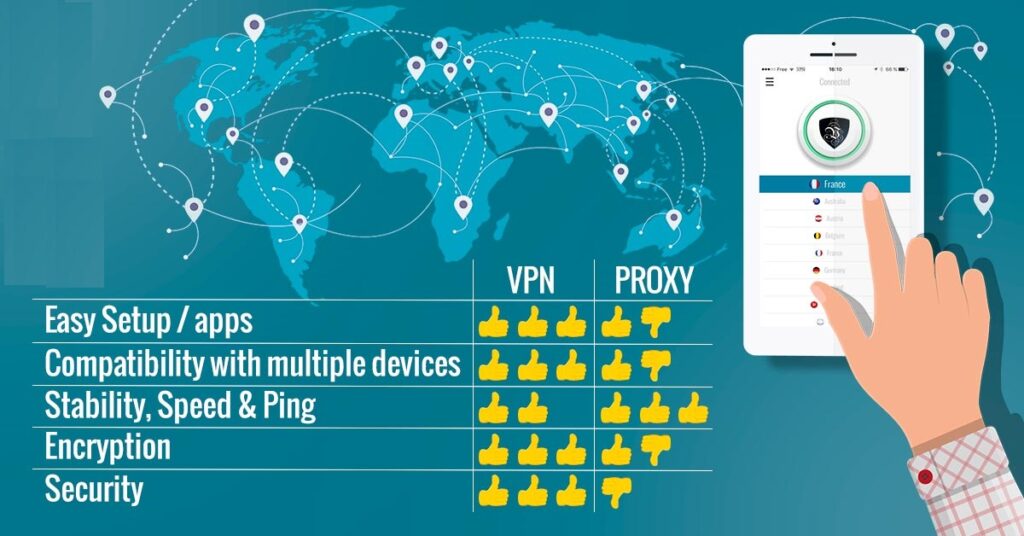
Proxy Vs. VPN: Which One is Best For You?
Both VPN and Proxies have their own set of merits and demerits that are worth considering before using. Therefore, we leave the choice on you so that you can think independently and choose wisely. However, we will make a table below with the full set of features that will make your choice evermore clear.
Below is a table with total set differences between the two.
| Proxy | Virtual Private Network |
| They work on the application layer | VPNs tunnel the whole device |
| Works faster due to less workload | Works slower due to higher workload and capacity |
| Data transferred is not Encrypted and can be a threat sometimes | Data transferred is fully Encrypted |
| Good for gaming as there are no ping issues reported | Not at all good for gaming, poor ping performance |
| Free proxies do work well | Free VPNs are a headache |
| Does not disconnect easily and suitable for long term usage | Disconnects frequently in sessions of 10-15 minutes |
| They interchange IP Addresses between different users | They provide complete new IP Address every time for each user |
| Not safe and sometimes fails to connect with banned sites | Always connects and safe to communicate with banned websites |
Wrap-Up
This was a comparison guide between a VPN and a Proxy and which one offers the best price to performance ratio. After reading our guide carefully, users will be able to analyze their requirements and thus put a value bet on their pocket. We hope this guide was helpful to you. If you have any queries or feedback, feel free to comment down below with your Name and E-mail ID. Likewise, check out our iPhone Tips and Tricks, PC tips and tricks, and Android Tips and Tricks for more such tips and tricks. Thank You.