Google is now getting closer to officially and publicly announcing the latest iteration of Android OS called Android 12 in a few days or so at the time of writing this article. Currently, the Android 12 Public Beta build is getting a couple of custom firmware already after releasing the Android 12 AOSP code officially. Now, if you’ve already rooted and flashed firmware on your handset, check out How to Pass SafetyNet on Rooted Android 12.
Well, SafetyNet is a security feature of Google for its newer generation of Android OS running smartphones and tablet devices that basically prevents a rooted Android device user from using banking-related apps or making transactions in most cases due to the security vulnerability. Although Android 12 is more focused on Material You design and plenty of customizations, useful features, etc, some users might find rooting more helpful.
Also Read
In that scenario, if you’re also going to root your Android 12 device or have already done it then you may find out that the device SafetyNet didn’t get bypassed on Android 12, unlike its previous generations. SafetyNet is an API that comes integrated into the Android OS by Google to check whether your handset has been modified or not. If it checks right then your device will be able to open or use some security-centric apps properly.
Page Contents
What means SafetyNet Fails?
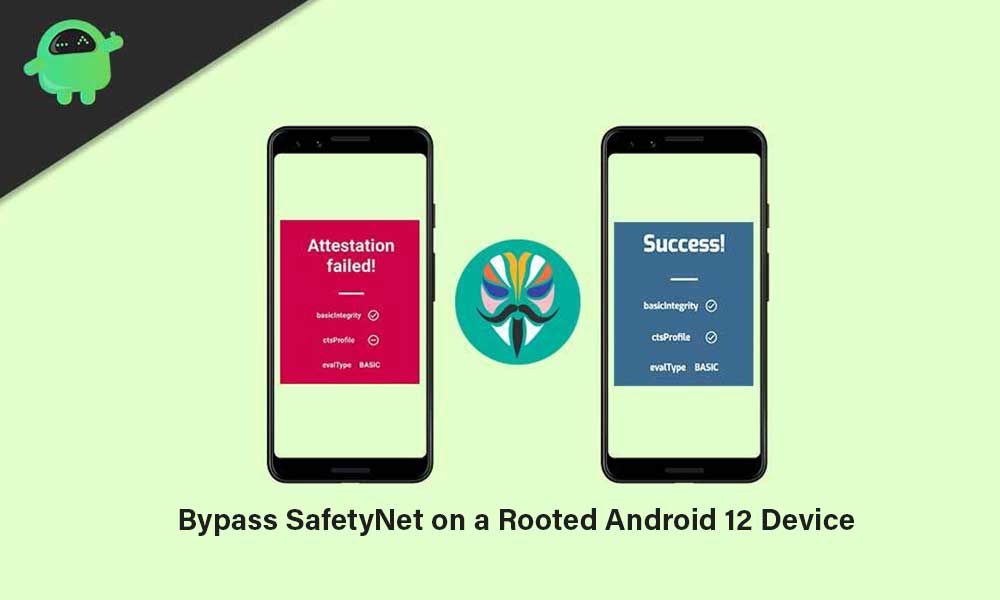
When SafetyNet fails to check the system as well as a hardware-based attestation to ensure integrity, your device won’t be able to use most of the online banking applications, streaming services like Netflix, Pokemon Go, and more.
Using the Magisk root method, it was quite easy for users to avoid or bypass SafetyNet in previous Android operating systems. Now, it seems that avoiding SafetyNet becomes quite hard with each Android release.
How to Pass SafetyNet on Rooted Android 12
Luckily, there is a possible way to bypass SafetyNet on your Android 12 handset that you’ve recently rooted. We’re assuming that you’ve already rooted your device via Magisk and have already installed the Magisk App on the handset. Now, head over to the guide below to follow all the steps properly.
Disclaimer: GetDroidTips won’t be held responsible for any kind of issues that may happen on your device during/after following this guide. You should know what you’re doing and proceed at your own risk.
Read Also: 10 Reasons to Root Your Phone in 2021
1. Install MagiskHide Props Config
- Open the Magisk App on your rooted Android 12 device.
- Now, go to the Modules section > Search for MagiskHide Props Config.
- Now, tap on the Download icon next to it > Tap on Install.
- Wait for the installation process to be completed.
- Once done, make sure to tap on the Reboot button at the bottom right corner of the screen to restart the system.
2. Force Basic Attestation
- Now, you’ll have to install any terminal emulator app on your Android 12 device from the Google Play Store. [You can get the Termux app]
- Open the Termux app and type in the following command:
su -c props
- It’ll give you SuperUser access > Just tap on Grant to enable it.
- Next, it’ll launch the MagiskHide Props Config inside the terminal itself.
- Type 2 (number) and hit Enter to Force BASIC Key Attestation.
- It’ll take you to the Force BASIC Key Attestation page. Here the default value will be seen as Nexus 5.
- You can choose Nexus 6P or Pixel 3A to pass the SafetyNet feature in most cases.
- So, once chosen any of the models, type d (Yes) as per the on-screen instructions and hit Enter.
- Now, type 7 (Google) and hit Enter.
- Then make sure to type 5 (Google Nexus 6P) and hit Enter.
- It’ll now ask you to confirm the selected value. Type y (YES) and hit Enter.
- Finally, you’ll need to reboot the handset by typing y (YES) and pressing Enter.
3. Enable MagiskHide
- Once your device boots into the system, launch the Magisk App.
- Now, tap on the Settings icon at the top right corner of the screen.
- Then scroll down to the Magisk section > Turn ON the MagiskHide toggle.
4. Install Riru Module
- Next, you’ll have to install the Riru Module from the Magisk App which is also necessary for bypassing the SafetyNet feature.
- Open the Magisk App > Go to the Modules section.
- Search for Riru and tap on the Download button next to it.
- Now, tap on Install and wait for the installation process to complete.
- Once done, tap on the Reboot button at the right bottom of the screen.
Must Read: How to Enable Developer Options and USB Debugging Running on Android 12 Phones
5. Flash SafetyNet Fix
A huge thanks to XDA Senior Member kdrag0n for creating this module that basically completes the bypassing SafetyNet (BASIC attestation) process properly. To do so:
- Click on this GitHub link to download the Universal SafetyNet Fix Magisk Module on your device.
- Open the Magisk App > Go to the Modules section.
- Now, tap on Install from Storage > Browse to the Universal SafetyNet Fix Magisk Module that you’ve downloaded.
- Then select the Universal SafetyNet Fix Magisk Module to start flashing it.
- Once done, tap on the Reboot button at the bottom right side of the screen.
- Finally, launch the Magisk App > Tap on Check SafetyNet > If it prompts to ‘Download Proprietary Code’ then tap on OK to allow.
- Voila! You’ll see that your device has been passed all three SafetyNet protocols (basicIntegrity, ctsProfile, and evalType BASIC).
This is how you can systematically bypass Google’s SafetyNet security feature on your rooted Android 12 handset. if you’re facing errors then make sure to choose a different device model between the mentioned ones and try performing all steps again one by one.
That’s it, guys. We assume this guide was helpful to you. For further queries, you can comment below.