Now a day, billions of people are using Facebook and new users keep on joining regardless of security concerns. We share our moments, thoughts, birthdays, locations, birth, and death. We use it as a tool for connectivity. Sometimes, we forget that there are people who may use our public information against us.
Also Read
How to Find If Someone Else Is Using Your Facebook Account?
Fix: Messenger Video Call Closing Automatically on Android and iPhone
How To Fix If Facebook Account Temporarily Locked
How To Download All Photos From Facebook
Who Blocked You on Facebook, How to Find?
What Does OBJ Mean on Facebook?
Facebook Messenger Not Working or Sending Messages | Server Outage?
Fix: Facebook Account Locked Due to Suspicious Activity
How to See Your Facebook Password Without Changing It?
-
Page Contents
Is it possible to hack a Facebook account?
Facebook account passwords can be stolen via the user’s phone number or email address. It doesn’t matter how many security measures you have applied to protect yourself, hackers can steal your login details. The main reason is faults in the SS7 network that allow the hacker to hijack your social media accounts. SS7 network relies on text messages exchanged over it rather than origin. So, hackers can divert your messages and calls to their own computers easily.
-
The main available ways of getting access to Facebook
Not only Facebook, hackers can target the users of Google accounts and Twitter too as these services are also using verify via SMS method. Here, the problem is not with the security features provided by Facebook. This is due to the reason: the telecom network (SS7) has design issues. It is recommended by Facebook to turn on the log in approvals feature in your account settings. It is a 2FA (two-factor authentication). So, if anyone has your phone number, still would not access your account without a password.
Add emails for account recovery. Avoid phone numbers. Use communication apps that offer end-to-end encryption features. Here is a list of possible ways to access Facebook account that you should go through:
-
Using a Spy App

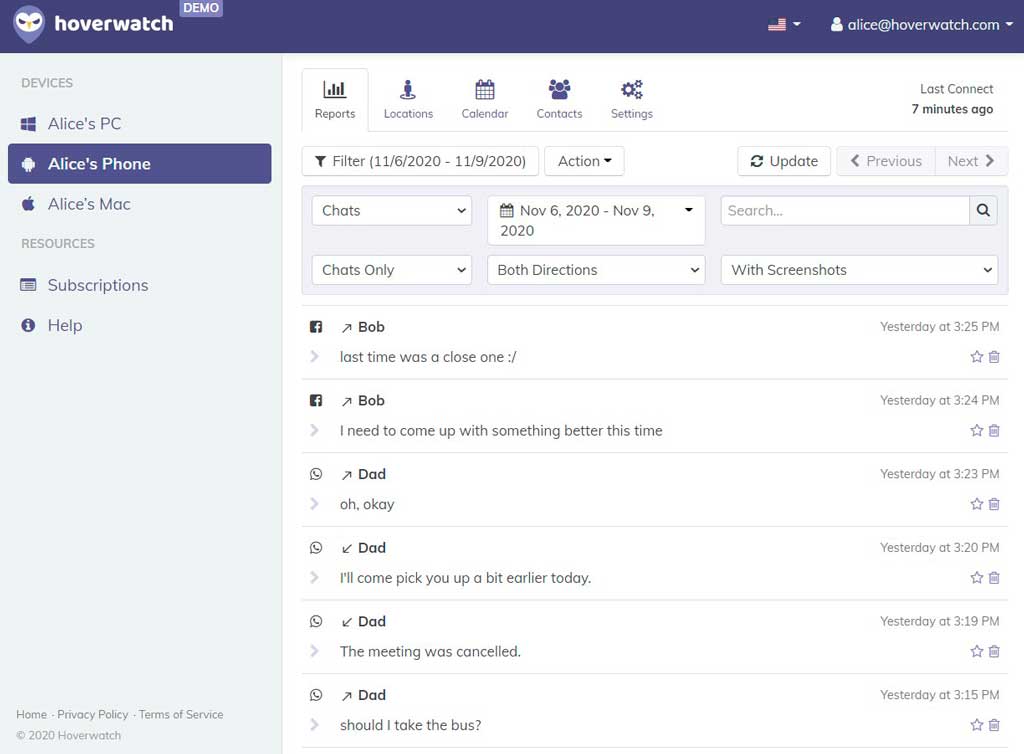
Facebook and Messenger accounts can be hacked quickly using a spy app, such as Hoverwatch. This facebook spy chat messenger tool saves all messages, images, audios, and videos from WhatsApp and Facebook messengers.
Using Android OS, messages are saved automatically. There is no need to root your device (phone or tablet). Follow three simple steps to try this app:
-
- Sign up on official website Hoverwatch.com for free
- Get the app by following simple instructions
- Install on the victim’s device
Hoverwatch works in invisible mode i.e. victims are unaware of being tracked. This method has limitations too.
You have to access the target device physically for spy app installation. If the victim loses his device (phone or tablet), the app has to be reinstalled to continue the tracking process.
-
Free hacking websites
The term “Hacking” doesn’t mean to gain unauthorized access by stealing someone’s password. It more about understanding the functioning of the Facebook website, its database system, languages, and scripts, used to develop the website.
When you search for “Facebook account hacking” on Google and got a list of tools and websites offering their services for free. There is a need to understand if it was so quick and easy to hack a password then Facebook would stop its business.
Yes, you are thinking right! All the sites claiming to hijack passwords just by typing a user name are illegal and fake. After submitting a user name or email address, they all may lead to some survey or ask to download some harmful software. They may also lead to annoying ads. All of these free hacking websites are no longer operational.
-
Hiring an Ethical Hacker
There come certain situations in life when people think about hiring an ethical hacker to get rid of their trouble.
- When you are seeking for recovering lost email passwords
- When your social media (Twitter, Facebook, etc.) account passwords are stolen
- When there is a need to track smartphone services
- When you are looking for monitoring the GPS location of someone
- When you are in doubt, your spouse is cheating on you.
- When you are stuck with cryptocurrency fraud and need to investigate.

Most of the people get hesitant while contacting to a hacker. There are some trusted agencies in the market, which may provide you, right hacker, for the right service. One of the popular agencies is spyandmonitor.com offering trusted services from ethical hackers.
-
Phishing
It may a difficult method for non-tech savvy. But it is the most common way to steal someone’s login cardinals now a day.
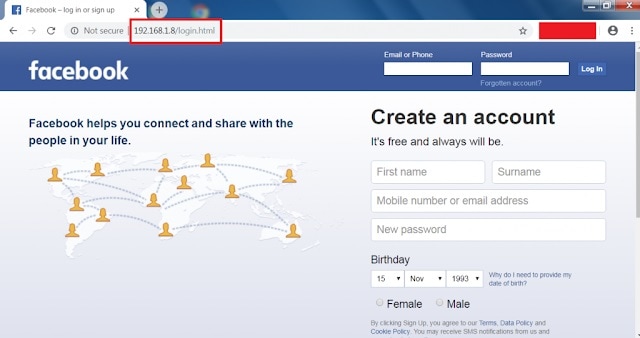
The attacker creates a Facebook login page that looks like the original login page. Such a fake page is called a phishing page and you may receive its link via SMS, email, or other social media platforms.
If you log in through a phishing page, your cardinals (email/phone no. and password) will be sent to the attacker instead of the Facebook server. To hack someone’s account using this method requires web hosting and login page designing.
The URL of the fake login page may seem like https://192.168.1.8/login.html/ rather than facebook.com. Be careful while clicking on the link receiving via SMS, email, or social media. Install anti-virus or web security software in the case of Windows OS users.
-
Keylogger
As the name suggests, a keylogger logs the keystrokes made by the user on the keyboard. Hence, it captures the username and password of the Facebook messenger being undetected by the user. In the case of a software keylogger, you have to install it on the victim’s device.
It will send you a summary of keystrokes through email. Installing anti-virus software, using firewalls, and avoiding third-party apps will keep you safe from software keyloggers.
-
Password reset
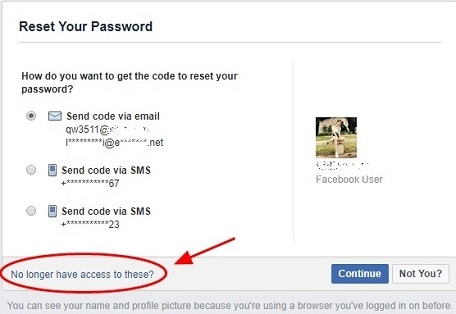
If an attacker knows the victim personally then the Facebook account can be hijacked very easily by resetting the password. You just need to know the victim’s email address that can be easily got by viewing the victim’s profile if added there.
Then click on Forgot Password >> email address >> this is my account >> No longer have access to these? After that, an attacker needs to make an intelligent guess to bypass the Facebook security question check.
It would be easy to guess if the attacker knows the victim personally.
-
Social Engineering
Being a popular social network, Facebook is a central point for social engineering attacks. Such an attack entails the human psychology factor. A hacker may communicate via email, Facebook, or WhatsApp messenger that fears the recipient.
It is a kind of psychological trick where the victim leaks sensitive data in fear or may click some harmful link or open some malicious file sent by the cyber attacker. End users should learn data security tips to keep themselves safe from social engineering attacks.
-
Man-In-The-Middle (MITM attack)
Attackers create a free Wi-Fi network. When users get connected with this network, attackers steal their sensitive information like id and passwords of Facebook messenger, Twitter, etc. To prevent a Man-In-The-Middle attack, do not connect to any open Wi-Fi network.
-
Signaling System Number 7 (SS7)
Using the SS7 attack, hackers can exploit design flaws in the network and hack users’ sensitive data. Not only social media (Twitter and Facebook) account passwords, but bank accounts have also been hacked via this technique.
It enables hackers to get the same level of access to information as security services. SS7 is considered to be the most advanced encryption used by cell phone networks. Still designing flaws in this network has been in news since 2014. To prevent yourself from an SS7 attack, use communication apps with end-to-end encryption.
-
Conclusion
For any Facebook account, passwords act like a gatekeeper. Hacking passwords is an illegal practice that may lead to unpleasant results.
To protect your children from online predators, it is recommended to use some official monitoring app like Hoverwatch. You may also use it to protect your company’s sensitive data from getting leaked.
With Hoverwatch tracking facebook messenger, you can monitor audio calls and text messages being received or sent, videos, pictures, Twitter, Facebook messenger, and Whatsapp accounts, and geographical locations in a legal way.